Table of Contents
What is Cybersecurity?
Cybersecurity is a process used to protecting digital devices, networks and information from online viruses, threats or attacks. Its main functions are as virtual security system, protecting your data and privacy against hackers, viruses and other dangerous malware or programs.
Cybersecurity uses of many techniques and tools, helps to ensure that your online activities such as browsing, shopping and communication, stay safe and free of illegal access or harm. It is an important part of our digital life because is keep safe all digital devices from unwanted viruses which are interconnected world of the internet. Cybersecurity is a cover that protects your digital the world. Cybersecurity is like a locking your home door to keep criminals out, employs specific locks and alarms to keep hackers and viruses out of your online data. So, when you are shopping online, chatting with friends or checking your bank account, cybersecurity acts as your digital bodyguard, ensuring your online safety.
Fundamentals of Cybersecurity
When technology develops, cybercriminals issues are increasing rapidly. Because the threat environment is continuously changing and increasing, individuals and organizations must remain aware and aggressive in their cybersecurity efforts.
• Key objectives of cybersecurity :
The main aim of cybersecurity is to ensure system and data confidentiality, integrity and availability. Only authorized persons have access to sensitive information, while integrity ensures that data remains unmodified and trusted. Availability is concerned with making systems and resources available when they are required.
• Types of cyber threats :
Cyber threats comes in a various forms, many of which target vulnerabilities in computer systems and networks. Understanding of these threats is essential for creating effective cybersecurity precautions. Here are three common types:-
1. Malware:
Malicious software is designed to harm or gain unauthorized access to computer systems. This includes viruses, worms, ransomware and more.
2. Phishing attacks:
Fraud emails, messages or websites that confuse users into revealing personal information like passwords or credit card numbers.
3. Social engineering:
The manipulation of people using psychological techniques to obtain illegal access to systems or information.
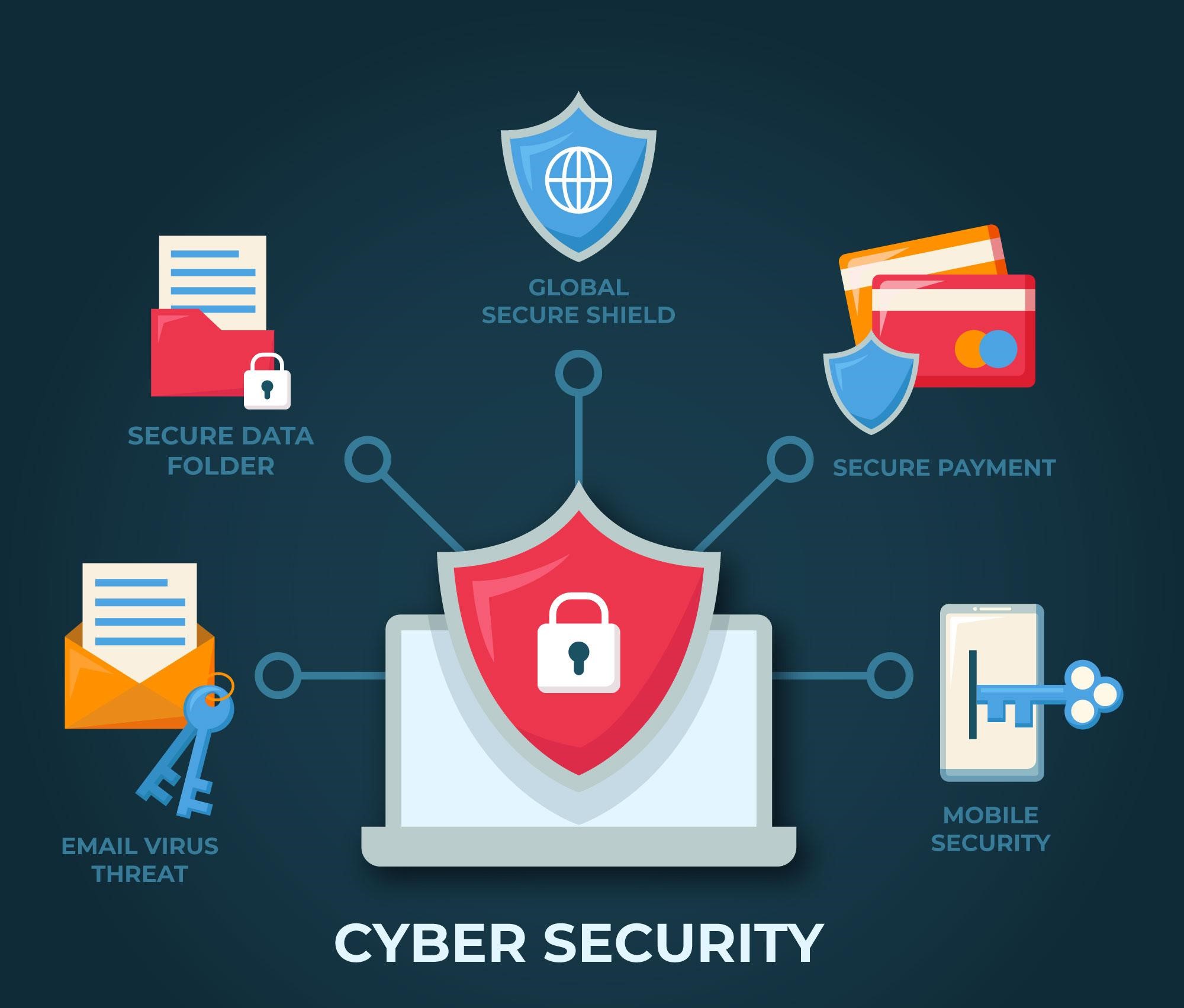

What are the three goals of cybersecurity?
1. Confidentiality:
Confidentiality is type of keeping your online data, information in safe mode. It means only the individually you trust have access to your personal information such as passwords, credit card information or private communications. Cybersecurity makes difficulties to prevent intrusions such as hackers from viewing your digital data.
2. Integrity :
It gives guarantee that the information which you send or receive hasn’t been tampered with during its passing through cyberspace. Cybersecurity works to make sure that your messages, files, or data remain unchanged.
3. Availability :
Availability is similar to having your phone charged and ready for use anytime you need it. Cybersecurity ensures that the internet services and systems on which you depend on such as websites, apps and email which are constantly available. It prevents threats that might break or make these services not accessible and keeping your digital life running smoothly.
In short, cybersecurity acts as a guardian for your online adventures, keeping your secrets safe, your information unchanged, and your digital tools at reach. It’s a digital shield that allows us to confidently traverse the internet, guaranteeing that our online experiences are safe and entertaining. So, keep these three cybersecurity superheroes in mind — confidentiality, integrity, and availability – and let them be your guardians in the digital world.

Components of a Strong Cybersecurity Strategy
• Risk assessment and management:
It is critical to identify and understand potential dangers before implementing any security measures. This involves identifying vulnerabilities, evaluating their significance and prioritizing measures accordingly. It defined risk management methodology helps organizations in properly allocating resources.
• Security policies and procedures:
The establishment of full security rules and processes acts as an essential component for a successful cybersecurity strategy. These rules should cover topics including password management, access controls, incident reporting, and data handling. To adapt to evolving threats, regular review and updates are required.
• Access control measures:
It is critical to control access to sensitive data and systems in order to prevent unwanted access. Implementing strong authentication mechanisms such as multi-factor authentication and limiting privileges based on role.
• Network Security:
Network security is used to secure your web based traffic, online data, information or digital systems. It basically focuses on protecting the infrastructure and data transmitted over networks.
There are below components contributes in network security:-
1. Firewall :
Firewalls act as a barrier between internal and external networks which used for inspecting and filtering incoming and outgoing traffic. It comes in hardware and software that deny all unwanted traffic until and unless you have a policy to allow it.
2. Intrusion detection systems (IDS) :
Intrusion detection systems (IDS) monitor network traffic for suspicious activities, alerting administrators to potential threats. IDS is passive monitoring solution for detecting a cybersecurity threats to an organization. If a potential intrusion is detected, the IDS generates an alerts that notifies security to investigate the incident and take immediate action on that.
3. Intrusion prevention systems (IPS) :
IPS is used to take an action to block any types of threats to protect systems or network from unknown viruses or vulnerabilities. IPS solutions used to detect also actively block and prevent potential threats from entering a network. By monitoring network traffic in real-time, IPS solutions provide an additional layer of security.
4. Virtual private networks (VPN) :
VPN is technology used to connect securely two or more networks remotely over the internet. VPNs allow secure remote access to private networks over the internet. By encrypting data transmitted between a user and the network, VPNs ensure confidentiality and integrity.
5. Endpoint Security :
Endpoints devices such as computers, laptops and mobile devices, represent potential entry points for cyber threats. Protecting these endpoints is important for overall cybersecurity.
6. Anti-malware solutions :
Installing and upgrading anti-malware software on a regular basis helps in the detection and removal of harmful software from endpoints. These solutions provide protection against viruses, spyware, and other forms of malware.


Requirement to protect from Viruses
• Regular software updates :
Regularly updating software and applying accurate patches is important for vulnerabilities. Outdated software can become an easy to target for attackers.
• Data encryption :
Encrypting is method is used to convert normal data into unreadable format. Encrypting sensitive data during transmission and storage adds another layer of security. Data is encrypted using encryption methods, making it unreadable to unauthorized parties.
• Mobile device security :
With the increased use of smartphones and tablets, it is critical to secure these devices. Implementing strong password regulations, allowing remote deletion capabilities, and utilizing encryption technologies all contribute to the protection of sensitive data on mobile devices.
Requirement for Web Security
Web security means to protect our web based data, information, traffic from unknown viruses, threats. It making sure websites and web applications are safe from online attack from hackers.
Types of web security as below:
• Secure browsing practices:
Safe browsing involves being aware of unexpected websites, avoiding downloading files from unknown sources, and cleaning browser caches and cookies on a regular basis. These procedures reduce the probability of malware infestations.
• Install SSL (Secure Socket Layer) certificates :
SSL certificates protect communication between web servers and browsers by encrypting data during transmission. SSL-enabled websites display a lock icon, indicating a secure connection.
• Understanding of cloud vulnerabilities :
In order to solve cloud-specific vulnerabilities, it is necessary to be aware of potential threats such as insecure APIs, data breaches, and hacking of accounts. Understanding these risks allows organizations to take appropriate security measures more proactively.

Social Engineering and Human Factors of Cybersecurity
Cyber attackers frequently use social engineering to target human weaknesses, highlighting the need of addressing human elements in cybersecurity.
• Types of social engineering attacks :
Phishing emails and phone scams, as well as cloning and teasing strategies, are examples of social engineering attacks. Individuals and organizations can identify and manage possible risks by being aware of these approaches.
• Employee awareness and training programs :
It is critical to educate staff about risks associated with cybersecurity and provide training on recommended practices. Creating a security awareness culture permits individuals to recognize and report potential dangers, as well as avoid falling subject to social engineering attempts.


Security in the Internet of Things (IoT)
The Internet of Things is a network in which multiple devices are connected with each other to communicate and share data via the internet. These devices include everything from smart kitchen gadgets to smart watches and industrial equipment.
The IoT devices introduces new challenges to cybersecurity. Protecting the connected world requires below aspects :-
• Risks associated with IoT devices :
IoT devices frequently have poor security protections and are vulnerable to a variety of threats. Vulnerability in IoT devices can result in privacy violations, data exposures, and even harm to people.
• Securing IoT infrastructure :
Implementing strong authentication techniques, routinely updating software, and providing secure communication routes are all part of protecting IoT infrastructure. To reduce risks, it is critical to apply security-by-design principles to IoT device development.
• Security of Artificial Intelligence (AI) :
AI technology has the potential to improve cybersecurity by automating threat detection and better incident response. However, AI can be used by hackers, stressing the importance of proactive defensive solutions.
The Future of Cybersecurity
• Potential threats on the horizon :
New risks will come up as cybercriminals advance. To prevent harmful activity, cybersecurity experts must remain ahead of developing dangers, continually adjust their strategies, and develop fresh ideas.
• Advancements in cybersecurity technology :
Technology will continue to be important in cybersecurity. Artificial intelligence, machine learning, and behavioral analytics advancements will enable more efficient threat identification and response.
• Shaping a secure digital future :
Collaboration between industry, government, and individuals is required for defining a secure digital future. highlighting cybersecurity education, promoting responsible technology usage, and creating a culture of awareness and accountability will all help to make the digital world a safer place.